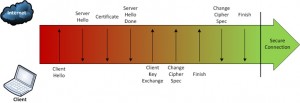
In the previous post I talked about how web browsers connect to the server and how a negotiation is initialized between server and client to establish a secure connection when the HTTPS protocol is used.
In this post I wil explain the SSL/TLS protocol and how a client (computer, smartphone, tablet, terminal, etc) and server can encrypt the data sent and received by an HTTPS connection.
Continue reading HTTPS and the TLS handshake protocol.
Category: Cryptography
Web Browsers and HTTP/S connections

This is the first of a series of posts about HTTP/S that you will find in this blog during the next days. I will explain technical aspects about these protocols, how they work, how to test and validate connections, sites and certificates. I will also write about the encryption algorithms and more.
Continue reading Web Browsers and HTTP/S connections
The Google Chrome Netbooks security
![]()
Recently Google announced its Google Chrome netbooks aka Chromebooks. They have great features like 3G support, boot time of seconds, automatic updates, review of core files integrity on every boot and more. With all these new functionalities on netbooks the security is extremely important because they have no experience with this set of technologies and they don’t know how people will take these changes and how “hackers” will take this new challenge.
Let’s review some of the security concepts and possible cons within the Chromebook.
Continue reading The Google Chrome Netbooks security