A new version of the OpenSSL reference has been released.
These are the changes:
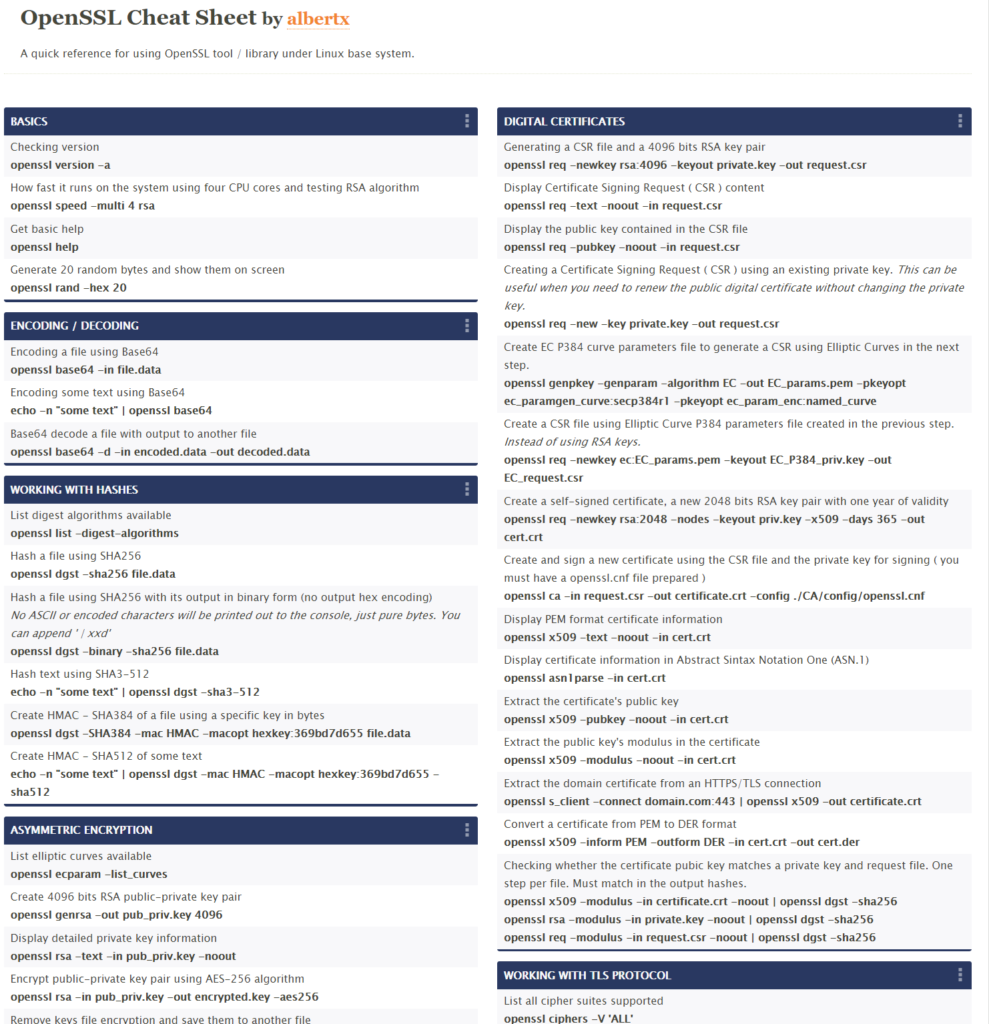
- Asymmetric encryption: Changes in how to export the public key to be consistent with the encryption command using RSA public key.
- Asymmetric encryption: Encrypt a file using RSA public key.
- Asymmetric encryption: Decryption of the previously encrypted file was included.
- Symmetric encryption: Changes in the decryption of a file using another file as the key, instead of a password.
- Digital Signatures: Signing a file using SHA-256 and RSA private key.
- Digital Signatures: Verifying the signature previously generated using the RSA public key file.
- Working with TLS protocol: Extract the domain certificate from an HTTPS/TLS connection.
- Working with TLS protocol: nmap command: Display enabled cipher-suites over an HTTPS/TLS Connection.
- Working with TLS protocol: nmap command: Display enabled cipher-suites over a TLS (HTTPS) Connection using SNI.